BeerCon 2
A fun filled virtual day of talks facilitated by The Beer Farmers and friends
Hold my Beer………. Con2
Just over a week ago I, and 27 other rookie speakers took part in a 2 day virtual conference put on by The Beer Farmers called BeerCon2. The Beer Farmers are, in their own words, “InfoSec rock gods and shitposters of global fame” and I tend to agree. Many of them play instruments and at least two had successful careers in the music industry - making them bona fide rock gods! However, this hugely understates the amount of good that they do within the community. Their slogan is #HereForYou - unlike some cybersecurity vendors that “Take Your Security Seriously” Here For You is really what The Beer Farmers are. Members have changed over their time, but the current band members comprise Mike Thompson, Ian Thornton-Trump, Scott McGready, Sean Wright, and John Opdenakker. Every one of the current and previous members are a force for good in the industry, in my humble opinion.
Along with the Infosec Happy Hour, (a cathartic weekly bit of fun infosec therapy, every Friday during lockdown), The Beer Farmers created BeerCon2 because, with the current pandemic, the chances for new speakers to get a chance to speak at conferences has significantly reduced. I for, one, am incredibly thankful they gave us rookies an opportunity and the rest of this will be a rundown of things from my perspective of giving my first cybersecurity talk.
Your 1st time might be daunting
The Beer Farmers had mentioned BeerCon2 and explained the reasons why. I thought this was an amazing initiative. Then they asked, “well where is your CFP”? I was quite stunned at this.
Although I’d worked in dev for a long time and worked to bring security practices into my dev role, alongside my studies, I didn’t think anyone would want to listen to anything I had to say. They were all very good at pushing me into giving my first talk on tech, let alone cyber, and I’m very grateful they did. All I can say to anyone thinking about it but is unsure…. DO IT.
Send that CFP in. If someone else else has spoken about it, then still… DO IT.
You have an interesting standpoint to share and no one else will have the same experience as you.
The Talk: Using OPSEC And Social Engineering As AWOL (A Way of Life)
Looking at previous talks from them I thought of something that I thought would be fun and something that I had lived. So I chose a narrative around many years of DJing in night clubs while underage and some of the stories from that time. Well, what’s that got to do with cybersecurity? It’s kinda OPSEC and social engineering. In a way…. Not really! A tenuous link, but at least it was something I thought I could talk about!
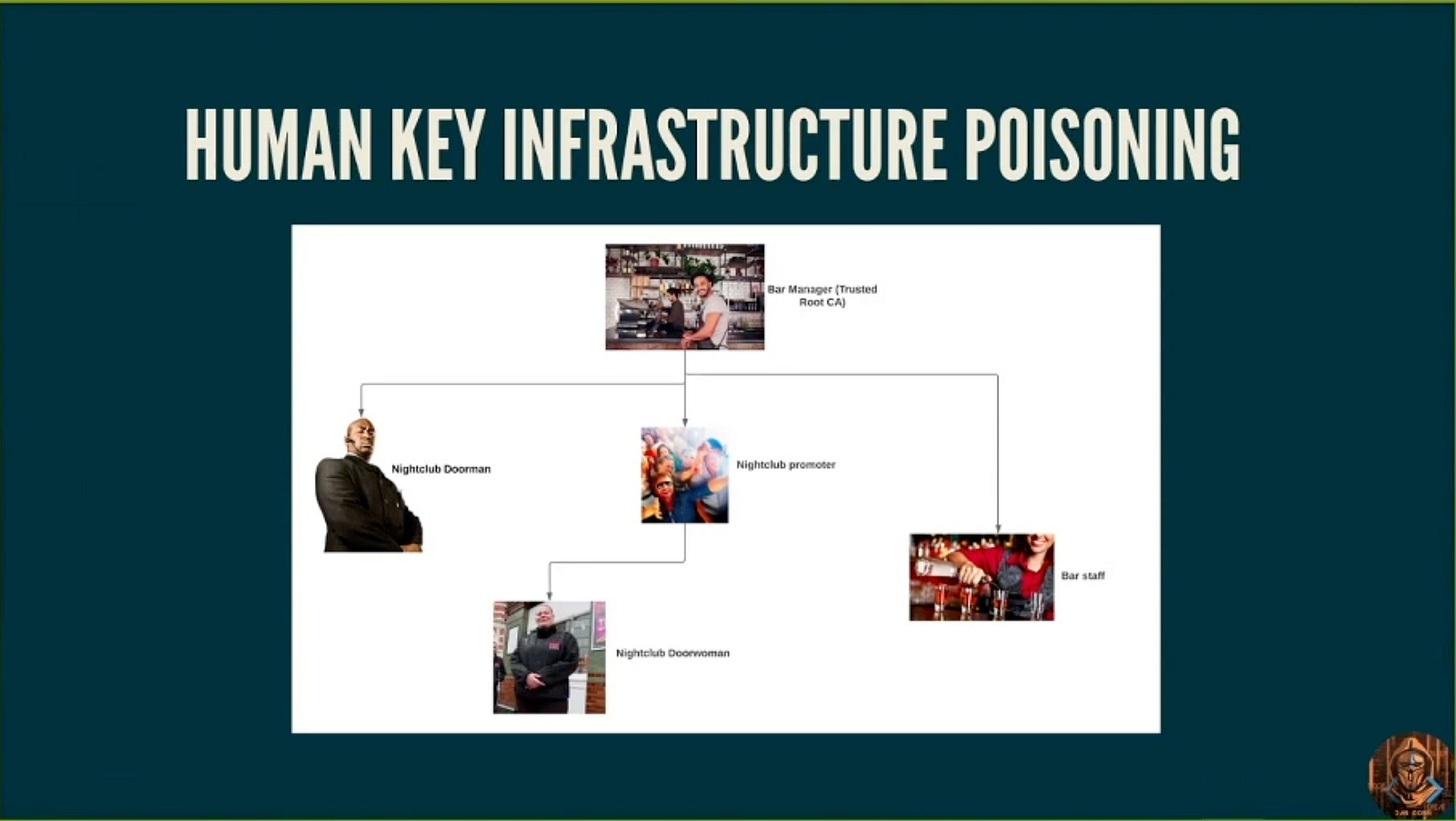
One thing that interested me when learning about social engineering was how you need to build trust in order to attack. I thought that if you think about chains of trust in humans, it’s a bit like how certificates are trusted in Public Key Infrastructure (PKI). If you poison a Root Certificate Authority (CA), then other CAs will accept the poisoned certificate which can lead to things that should not be trusted, to being so. Let’s consider that humans also have this tree of trust, a Human Key Infrastructure (HKI), perhaps. By using social engineering techniques, you can poison this HKI too meaning that you are trusted to do things that you shouldn’t be. In this example it’s being let into nightclubs underage, and getting to DJ at them. But it could also be someone in a business wishing to undertake corporate espionage.
Here’s a link to the talk if you fancy watching it:
The support acts are important
In the run up to the event there was a Slack channel where we could ask questions, arrange rehearsals via Zoom, and just be really supportive of each other. It was a lovely introduction to a new experience. Along with the support we had for each other, there was also a team of mentors and roadies who were so incredibly helpful. I think it’s important to mention them and I hope to remain friends with all of them:
Lennaert Oudshoorn, Gerrard Barrett, David McKenzie, James Bore, Zoë Rose, Claire Tills, and Sam Humphries
I also had a huge amount of support from someone I’ve never met but definitely consider a friend, Lisa Forte. I was honoured that she gave me permission to include her story of harassment within the cyber security industry as part of my talk. Although working in tech I have seen various isms and examples of toxic culture, I can not fathom why men (it almost always is men), especially someone in charge of security, can harass someone in this nature. I hope this is something that stops soon. Although Lisa was not an offical BeerCon2 mentor, she ran through my slides and gave me great advice to prepare me for my first talk, and I’m incredibly grateful for the time she gave.
Further to this Stu Peck was also kind enough to run through my slides and give permission for his quote on OPSEC to be used.
Final mentions of support go to Dan Card, Dan Ward, Francis Anderson, and Andy Holmes. These people truly are Infosec Twitter at their best. Danurday - every Wednesday a selection of us called Dan (and Andy under the name DanHy) say Happy Danurday - daft but something in this tough times gives me such a happy smile. Team Crofting - all of us trying to do exercise and replace our surname with Croft - Francis Croft, Andy Croft, Dan Croft, Lisa Croft! Daft yes. But combined with Zoom chats, talks, text messages from these and all the people above, I get a great sense of belonging, togetherness and happiness while all the world goes through some terrible horrible stuff.
Roadies, support, friends. Thank you ♥
The show finale
That’s enough of me. There were 27 other speakers over the two days and although I couldn’t watch all of the talks at the time, I am catching up with them now they’re added to a YouTube channel.
Check out the full playlist here:
I cannot stress how amazed I am that everyone in this playlist was their first time speaking. It truly was an inspiring event and hopefully they long continue.